Redes Privadas Virtuais(VPN)
3. Tipos de VPN
As seen on the part about VPN applications, there is a few different types of VPNs but different protocols exist. Each of these protocols can usually be used in all VPNs types.
As several protocols exist, and as some of them became obsolete very quickly, we decided to focus on the ones that we thought were the most important.
Moreover, some of the protocols use mechanisms that are so complex that a full report would be necessary to describe them in details. We tried to synthesize and present the most interesting aspects of each protocol.
Point-to-Point Tunneling Protocol (PPTP)
PPTP was created by Microsoft among other companies. Creates a tunnel and encapsulates the data packet. It is one of the most widely used VPN protocol. The authentication is done through a password.
This protocol opens two communication channels between the client and the server :
- The tunnel is instantiated by the first channel, which is a TCP connexion on the port 1723 of the server
- This TCP connexion is used to initiate and manage the second channel, which carries the data of the private network.
This channel uses the IP protocol to transmit GRE packets. The RFC 2784 specifies how GRE packets are exchanged :

As it is created by Microsoft, it is built-in on every Microsoft devices and so it is fast and easy to set-up, and has stable performance.
It is an old protocol, and several security issues were raised. Therefore, it is being replaced by newer protocols.
Layer Two Tunneling Protocol (L2TP)
This protocol combines features from two other protocols, PPTP, previously described, and L2F (which is now obsolete).
Using an UDP connection, L2TP packets (containing the protocol header) are exchanged between the L2TP tunnel between the client and the server. The packets are categorized as either control packets or data packets. Control packets are used to initialize, manage and terminate the connection, whereas data packets are composed of pure user data.
L2TP provides reliability features for the control packets, but no reliability for data packets. Reliability for the latter, if desired, must be provided by the nested protocols running within each session of the L2TP tunnel.
A same tunnel can carry several connections, so there is usually one tunnel between two equipments. Because of that, the packets need to get de-multiplexed upon reception. As a result of this extra work, the performance of L2TP decreases but in return it delivers highly secured transmission.
L2TP does not provide confidentiality or strong authentication by itself but relies on an encryption protocol that is passed within the tunnel. Usually, IPSec (described in the next section) is implemented along, to provide confidentiality, authentication and integrity for the data packets.
When it is used along with IPSec, L2TP becomes one of the most secure VPN connections available. We will now talk about IPSec that is now widely used in IPv4 and IPv6.
IP Security (IPSec)
IPSec is a suite of protocols of IPv6 that aim to secure IP communications by authentication and encryption of each packet sent over the network.
It includes mutual authentication at the beginning of the session, and exchange of cryptographic keys that can be used during the session.
IPsec supports :
- Peer authentication : Making sure that the communication is initialised between the right entities.
- Data-origin authentication : Once the connection is initialized, making sure that the packets received are part of the secured connection, and come from the right agent.
- Data integrity : Making sure that the data received is the same as the data sent. By calculating and comparing hash values, the sender and receiver will be able to check if changes have been made to the packet.
- Data confidentiality : Making sure that no one can read the data exchanged, using encryption.
- Replay protection : Protection against a specific attack, where the malicious agent blocks a transmission from the sender from being received by the recipient, stores the transmission, and uses it again later. The recipient will be expecting this specific transmission because it never received the first one which was blocked. By using sequence numbers for example, IPsec will not transmit any duplicate packets.
IPSec was first designed to be used with IPv6, but was then adapted for IPv4. It uses AES-256 bit encryption (other encryption protocols can be used as well), and has no known vulnerabilities. However, following the well known revelations of Edward Snowden in 2013, there are allegations that IPSec was compromised by the american NSA.
OpenVPN
Introduced over 15 years ago, OpenVPN is currently the only protocol that can be accessed through an open source application, and due to its popularity it has been built to work on some of the most popular user platforms such as macOS, Windows XP, Android, iOS and Linux. It uses SSL and TLS protocols to authenticate with a secure internet connection. As it is open source, everyone can read the code to try to find flaws to use, or to make sure that no flaw exist, or that no backdoor from any government is present.
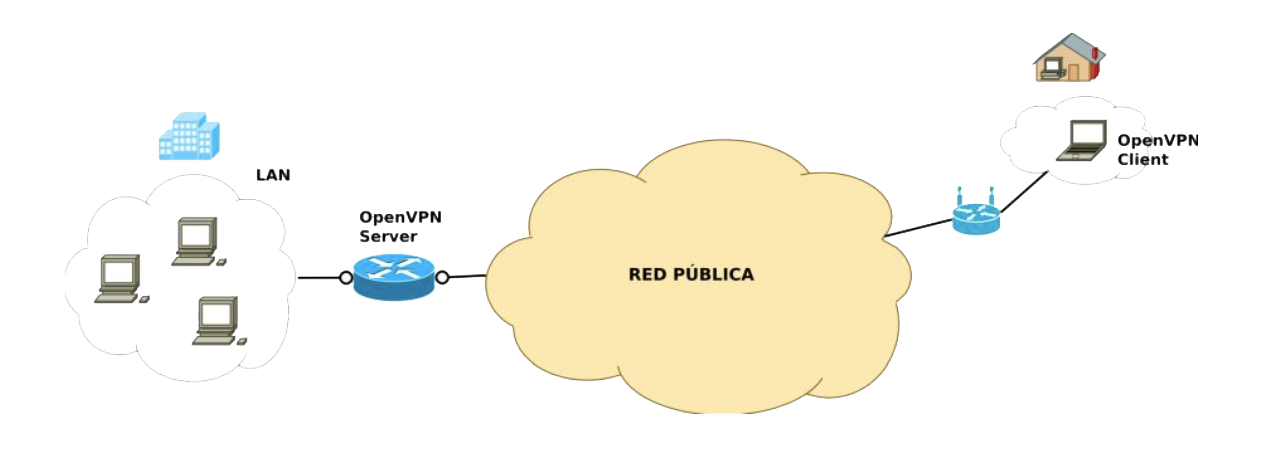
OpenVPN creates a TCP or UDP tunnel and then encrypts the data inside the tunnel, using the OpenSSL library.
OpenVPN allows flexible customization, meaning that OpenVPN clients can accomplish specific goals. For example, the authentication can either be through a pre-shared key, a public key infrastructure (PKI)/asymmetric cryptography, or a combination of username and passwords, according to the user goals. Let’s talk about the two first authentication solutions :
Using pre-shared static keys, the configuration is very simple but the problem comes when transmitting the key, you already need a secure channel, before having established it.
Using PKI, each side owns two keys, a public and a private one. If A wants to send a message to B, A encrypts the message using the public key of B. Once the message is encrypted, only the private key of B will be able to decrypt it. With this system, there is no need to share any key over a secured channel. Only the public keys needs to be exchanged, and there is no danger if someone malicious gets this public keys.
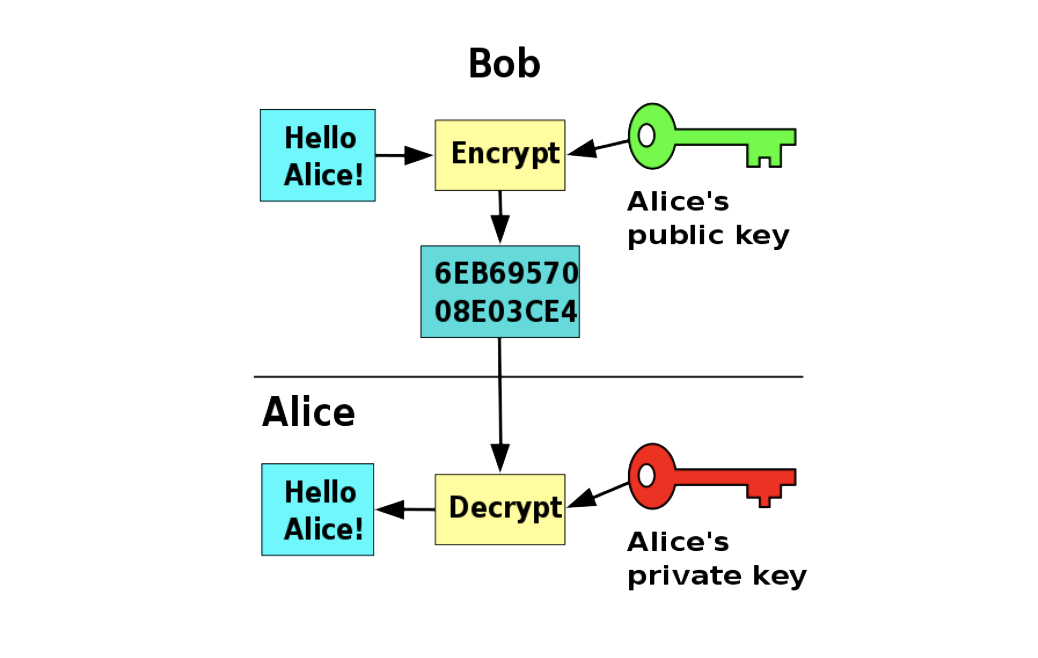
This latter solution is the default one used by OpenSSL (itself used by OpenVPN).


